How to Safeguard Your Online Presence as a Small Business Owner

Ah, the internet: the world’s favorite double-edged sword. Offering both boundless opportunities and serious threats, it’s a stage that’s truly Shakespearean in its drama and theatrics.
As a small business owner, you need to juggle both sides of the coin. It’s like being a superhero; fantastic powers come with enormous responsibilities!
You may have taken the first few steps toward securing your online presence. However, the evolving digital landscape calls for a robust online privacy protection plan, not superficial, run-of-the-mill, insufficient strategies that leave your business exposed to cyber threats.
In this blog, we’ll delve deeper into 15 ways to safeguard your online presence. Before you dive right in, develop a better understanding of the modern cybersecurity landscape. Our recent blog offers a closer look at the top cybersecurity issues for small businesses in 2023.
All done? It’s time. Let’s roll out the grand data protection and privacy plan!
1. Secure Your Business Website
If you want to plant a secure flag at the summit, you need shovels and spades. That’s cybersecurity for you in a nutshell.
No matter how pristine your online presence may be, an unprotected website will take you back to square one. If you haven’t turned your attention to online privacy protection for small business owners yet, jump on the bandwagon stat.
Think of your website as your online headquarters. You wouldn’t leave your physical store unlocked overnight, would you? So why would you leave your website vulnerable to cyberattacks?
First things first, it’s time to get HTTPS-ified. No, this isn’t some high-tech transformation. It’s about moving from HTTP to HTTPS, that is, from HyperText Transfer Protocol to HyperText Transfer Protocol Secure.
The little “S” makes all the difference in data protection and privacy.
![]()
Notice the tiny padlock icon next to the URL? That’s a superhero “S” at work. Its job is to ensure that the data transferred between a user’s browser and your website is encrypted and secure from any prying eyes.
There’s no rocket science here; getting HTTPS-ified is as simple as obtaining an SSL (Secure Sockets Layer) certificate and installing it on your website’s server. Many website hosting services offer SSL certificates as part of their hosting packages.
Once you’ve checked this box off the list, add another layer of protection: a security plugin. Think of these plugins as your digital security guards. They’ll arrive armed and fend off any cyberattacks.
Let’s consider WordPress websites. Security plugins like Wordfence and Sucuri are excellent choices. These plugins boast a range of features, including firewall protection, security scans, and so much more.
If a cybercriminal tries to break into your site, they’ll be stopped in their tracks. These plugins detect intrusion attempts, block the suspicious IP address, and send you an alert about the incident.
Sweet, right?
2. Protect Customer Data

In the business world, customer data is like the goose that laid golden eggs; it’s priceless. You’ve got names, email addresses, credit card details, and all types of information that helps you serve your customers better and grow your business.
But remember what happened in the story? People tried to steal the golden eggs. Similarly, cyber thieves are on the prowl for customer data. It’s your job to protect these golden eggs and maintain a stellar online presence.
Start by encrypting sensitive data. Payment gateways like Stripe and PayPal automatically encrypt sensitive data like credit card information.
When a customer makes a purchase on your website, the transaction details will be securely transmitted and stored.
Let’s visualize this. Say you run a pet supply store online, “Paws & More.” When Mr. Peter buys a fancy new collar for his poodle, his credit card information will be encrypted by Stripe. This will help keep it safe from any data thieves lurking in the cyber shadows.
All done?
It’s time to create a privacy policy next.
A privacy policy informs customers about the specific data you’re collecting, why you’re collecting it in the first place, and how you’re keeping it safe.
Etsy, a popular online marketplace, has a wickedly good privacy policy; it’s as clear and comprehensive as it gets. Instead of using complex jargon and confusing people, they’ve explained their data practices using simple, fuss-free, digestible language.
It’s tempting to collect all sorts of data about your customers. The more you know, the better you can cater to their needs, right? Well…not quite.
Each piece of data you collect is a golden egg you need to protect. As a rule of thumb, only collect information that you absolutely need.
If you run a clothing store, “Chic Threads,” you may need your customers’ sizes, preferences, and perhaps their birth dates (for birthday discounts), but you don’t need to know their pet’s names or favorite color.
Careful data collection will go a long way in helping you stay on track.
Once collected, data needs a secure home. Opt for services like Amazon Web Services (AWS) or Microsoft Azure to reap the benefits of secure, scalable, and affordable cloud storage solutions for small businesses.
Let’s stick to the “Chic Threads” example we mentioned earlier. Using AWS, you can securely store your customers’ data in the cloud. Features like automatic encryption and regular security audits will keep your data secure.
The outcome? Your golden online presence will become stronger over time, not weaker. This is one of the sharpest tools in the data protection and privacy toolkit.
3. Train Your Employees

Your team is the backbone of your business. But did you know it can also be the Achilles heel of your cybersecurity?
Let’s consider a hypothetical scenario. John, your star sales guy, is working late one night. He receives an email, seemingly from the HR department, asking him to confirm his login details. In his fatigue, he doesn’t notice the strange email address. He replies, and voila, your system is compromised.
This type of attack, known as phishing, is increasingly common. Training your employees to recognize and effectively respond to cybersecurity threats is a fundamental aspect of safeguarding your online presence.
Your employees often serve as the primary line of defense against cyberattacks. A workforce that’s well-educated in recognizing potential threats and responding appropriately is the most effective shield you have against cyber threats.
Training your employees isn’t and shouldn’t be a one-time thing. You can’t plan a cybersecurity and data privacy seminar and call it a day. Cyber threats are continually evolving, which means educating your team should also be a continuous process.
How can you go about this?
3.1. Regular Cybersecurity Awareness Training

Start with regular training sessions that cover the basics of cybersecurity, including how to recognize potential phishing emails, the importance of password security, and how to safely navigate the web.
Cybersecurity awareness training can significantly reduce the risk of successful cyberattacks by equipping your employees with the knowledge they need to identify, acknowledge, and avoid threats.
Let’s consider an example. Say your business operates an eCommerce website and employees handle sensitive customer data pretty much every day.
By conducting regular cybersecurity awareness training, you’ll help your employees become better equipped to recognize signs of potential data breaches or cyber threats. This could be anything from a suspicious email requesting customer data to unusual activity on your website that may indicate a hacking attempt.
3.2. Scenario-Based Training
Providing employees with hypothetical scenarios is a great way to help them understand the potential consequences of a cyberattack and grasp the importance of data protection and privacy.
This type of training encourages employees to think critically and solve problems. The outcome? They’re more likely to retain and apply the information they learn.
Let’s say your employees are trained to identify phishing attempts through a series of simulated emails. These emails are crafted to resemble a real phishing attack; they come with suspicious attachments, questionable sender addresses, and urgent requests for sensitive data.
Through this hands-on experience, your employees will become adept at identifying and safely dealing with potential threats.
3.3. Regular Testing and Assessment
Regular testing and assessment after each training session aren’t just important; they’re imperative when it comes to protecting your privacy online. This is a great way to ensure employees understand the material and are capable of applying it.
After all, the goal of training isn’t merely to provide information; it’s to change employee behavior and create a more secure online environment for your business.
For example, after a training session about password security, employees could be asked to demonstrate their understanding by creating a strong, secure password. Alternatively, you could conduct a surprise mock phishing attack to see how many employees fall for it.
This will help you determine whether the training was effective or not. If employees struggle to apply the knowledge provided in the training sessions, it’s time to change your approach.
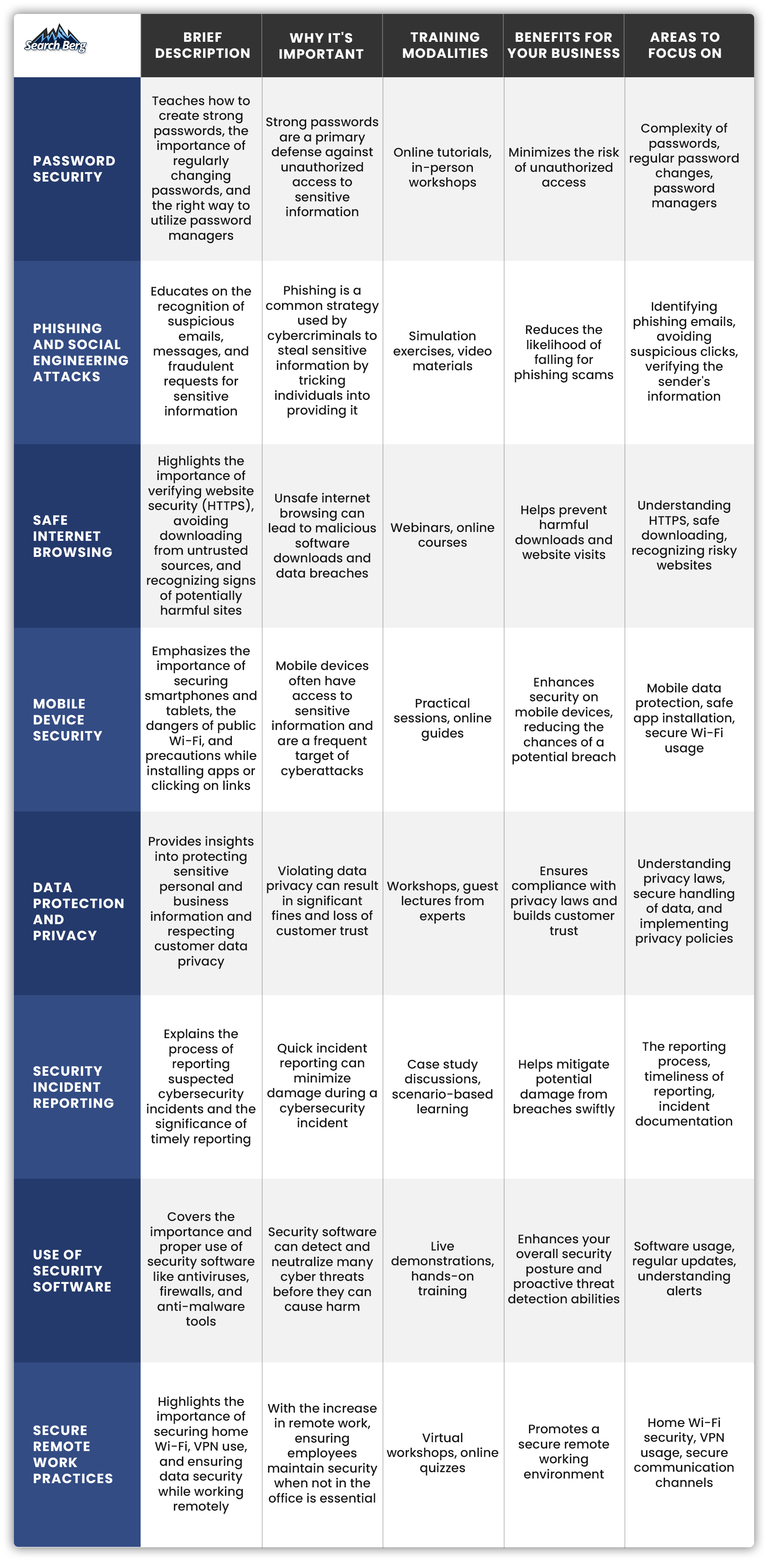
Use this table as a starting point. We’ve covered eight critical training topics and equipped you with a snapshot of each topic’s relevance, the modalities through which you can conduct the training, how each contributes to your business’ security, and the specific areas you should focus on for each topic.
4. Implement Strong Password Policies

According to Cybernews, the most common passwords in 2023 are “123456”, “123456789”, “qwerty”, “password”, and “12345”. If this is making your cybersecurity senses tingle, you’re not alone.
Implementing strong password policies is a fundamental and powerful way to safeguard your online presence. While it may seem basic, password security remains one of the most common areas where businesses, both large and small, are vulnerable.
Cybercriminals often exploit weak or easily guessable passwords and gain unauthorized access to sensitive business data. If your online privacy protection plan doesn’t have a section dedicated to password protection, you’re going about it the wrong way.
Let’s consider an example. “Jenny’s Jewels” is a small eCommerce store that specializes in handcrafted jewelry. The business owner, Mrs. Stewart, uses the birthdates of her children as passwords for simplicity and ease of memory.
An employee’s email account gets hacked due to a weak password. The outcome? Cybercriminals get their hands on sensitive company information, including customer credit card details. This leads to a severe data breach, financial loss, and reputation damage that Jenny’s Jewels struggles to recover from.
Take “Healthy Habits” as another example. The small health and wellness clinic’s receptionist shares her computer password with a new employee to expedite training. The password is also used to access the clinic’s patient database.
The new employee unknowingly enters this shared password into a phishing email scam. This results in a data breach that compromises the confidential health records of hundreds of patients. Healthy Habits lands in serious legal trouble due to the violation of privacy laws and endures significant reputation damage.
There’s an easy way to avoid all this, and it’s as simple as setting up a strong password policy. How can you go about that?
4.1. Enforce Password Complexity
Encourage the use of complex passwords that are hard to guess. A complex password typically includes a combination of upper- and lower-case letters, numbers, and special characters.
For instance, instead of using a password like “bakeshop123,” opt for a more complex password like “B@keShOp_2837SS!” The mixed cases, special characters, and inclusion of numbers make this password harder to guess.
Longer passwords are more secure. As a rule of thumb, set passwords with a minimum of 12 characters. Password complexity helps deter cybercriminals from guessing your password or using brute force methods (where they try many combinations in quick succession) to crack your password.
4.2. Regular Password Changes

Regular password changes can help prevent unauthorized access, especially in instances where a password may have been compromised without your knowledge.
Ideally, you should update your password every 60–90 days. When a password is changed, it must be entirely new, not a variation of the original password.
Reusing old passwords or making minor modifications to existing ones doesn’t provide the same level of security as setting a completely new password.
4.3. Two-Factor Authentication
Two-factor authentication (2FA) adds an additional sheath of security to your online accounts. In addition to entering a password, users must also verify their identity with another piece of information or physical token.
This could be a text message code sent to their phone, biometric verification, or an email with a unique link. This practice means that even if a cybercriminal gets hold of your password, they can’t access the account unless they also have the second authentication factor.
A huge sigh of relief, right?
4.4. Use of Password Managers
Password managers are software applications that store and manage your passwords. They generate, remember, and fill in passwords for you, significantly reducing the risk of human error.
These tools often generate complex passwords that users don’t need to remember, resulting in enhanced security. Moreover, most password managers use robust encryption, making it difficult for hackers to access the passwords stored within.
4.5. Prohibit Password Sharing
If you want to maintain robust cybersecurity, prohibit password sharing.
It may seem convenient for employees to share passwords, especially in small teams where roles and responsibilities often overlap. However, password sharing drastically increases the likelihood of unauthorized access and potential data breaches.
It’s akin to giving out the keys to your business freely!
Set a clear and strong password policy. Emphasize the importance of keeping passwords confidential and the potential consequences of non-compliance.
Employee training and regular audits are fantastic ways to reinforce this policy and promote a culture of individual responsibility for stronger cybersecurity.
5. Regularly Update Your Software

Outdated software is like leaving your backdoor open at night; it’s an open invitation for intruders.
If you want to enjoy enhanced data protection and privacy, regular software updates are a no-brainer. They’ll help you maintain optimal performance, prevent potential vulnerabilities, and enhance overall security.
Let’s break down the importance of software updates and understand how they work.
5.1. Patch Security Vulnerabilities
Software updates often include patches to security vulnerabilities that have been discovered since the previous version of the software was released.
Software developers regularly monitor for any weaknesses that hackers could exploit. When they find these vulnerabilities, they create patches to fix them, which are then released as part of software updates.
For example, let’s say you’re running a version of a web browser that has a security flaw. This flaw could potentially allow a hacker to install malware onto your system. By updating the software, you’re installing a patch that fixes this vulnerability and eliminates the threat.
In 2023, Apple released a patch for a security vulnerability known as ColdInvite (CVE-2023-27930) through an update to iOS 16.5 and iPadOS 16.5. This vulnerability followed a previous one, ColdIntro (CVE-2022-32894), both of which enabled attackers to escape the secure “isolation environment” of a coprocessor, a chip that helps the main processor complete tasks more quickly.
The attackers could then gain access to the iPhone’s kernel, a core part of the device’s operating system. By releasing this update, Apple managed to patch this security vulnerability and protect iPhone and iPad users from potential attacks.
5.2. Enhanced Performance
Updates also frequently include enhancements to improve the software’s overall performance. These enhancements can make the software run faster, reduce its demand on your system’s resources, and introduce new, more efficient algorithms.
Improved software performance not only ensures a smoother user experience but also indirectly contributes to your security posture. Faster and more reliable systems mean less downtime and fewer opportunities for cybercriminals to exploit any inconsistencies caused by software malfunctions.
An excellent example of software enhancement for improved performance is Python’s update from version 2 to version 3. The transition involved significant optimizations, including better memory management and improved speed.
For example, Python 3.8 introduced the “walrus operator” for assignment expressions that can simplify code and enhance execution speed. Efficient memory management in Python 3 also reduces the load on system resources, resulting in less downtime.
This indirectly contributes to better security as fewer system inconsistencies can be exploited by cybercriminals.
5.3. Access to New Features
Another advantage of regular updates is that they often provide new features or improvements to existing ones. These can help increase business efficiency by leaps and bounds.
While this point may not directly relate to cybersecurity and data privacy, keep in mind that many of these new features often include improved security controls. For example, an update may provide better user management features, giving you more granular control over who can access what within the system.
Microsoft’s Power Platform is an example of software that regularly provides new features. One significant update was the introduction of the AI-powered Power Platform Copilot.
This tool enhances developer productivity by providing generative AI capabilities for rapid website and application development, intelligent suggestions, and seamless integration of Power Virtual Agents chatbots into Power Pages sites.
The tool also simplifies the creation of data-centric forms and enables the customization of websites and applications. These features not only increase efficiency but also offer better security controls, e.g., the ability to manage users effectively through the platform.
You don’t have to shoot for the stars like Microsoft. As long as you’re regularly updating your software and unlocking new features, you’re on the right track.
5.4. The Perils of Outdated Software
Now that we understand the benefits of software updates, let’s cover the risks of not updating your software. Outdated software is on every cybercriminal’s radar. If you’re using outdated software, you’re essentially using a version that’s known to have vulnerabilities.
Hackers often target these vulnerabilities specifically because they know that many businesses delay or fail to apply updates.
The SolarWinds hack in 2020 serves as an example of the risks associated with outdated software. The cyberattack exploited vulnerabilities in the outdated SolarWinds Orion software, which hadn’t been updated in many instances.
As a result, numerous US government agencies and businesses were compromised, resulting in severe security and financial implications. The attack demonstrated the importance of regular software updates to patch known vulnerabilities and prevent such cyberattacks.
6. Use Secure Payment Systems

Picture this. You’re about to perform a daring high-wire walk across a towering canyon, teetering thousands of feet above the ground.
You have two options for your safety gear: a thin, frayed rope that’s been sitting out in the sun for weeks or a robust, state-of-the-art cable that’s been tested for strength and durability.
Which would you trust with your life?
The latter, right?
Think of your business transactions as this high-wire act, with the payment systems acting as your safety gear. Just as the cable safeguards you during the high-wire walk, a secure payment system protects your business and customer data during each transaction.
In the thrilling circus of online commerce, every transaction is a high-wire act. The sensitive information shared during online payments is as precarious as a high-wire walk. One wrong move, one tiny mishap, and it can all come crashing down.
Cybercriminals are waiting for a moment’s weakness to pounce and make a meal of your data: clients’ credit card details, personal identification information, and more. As a small business owner, the last thing you want is for your hard-earned reputation to be tarnished by payment fraud or data breach.
A secure payment system provides encrypted transactions, i.e., the sensitive data is turned into complex code as it travels across the internet. This encryption makes it extremely difficult for cybercriminals to read the information, even if they intercept it.
This is like sending a secret message in a language that only the sender and receiver understand, making it useless for anyone else who might intercept it.
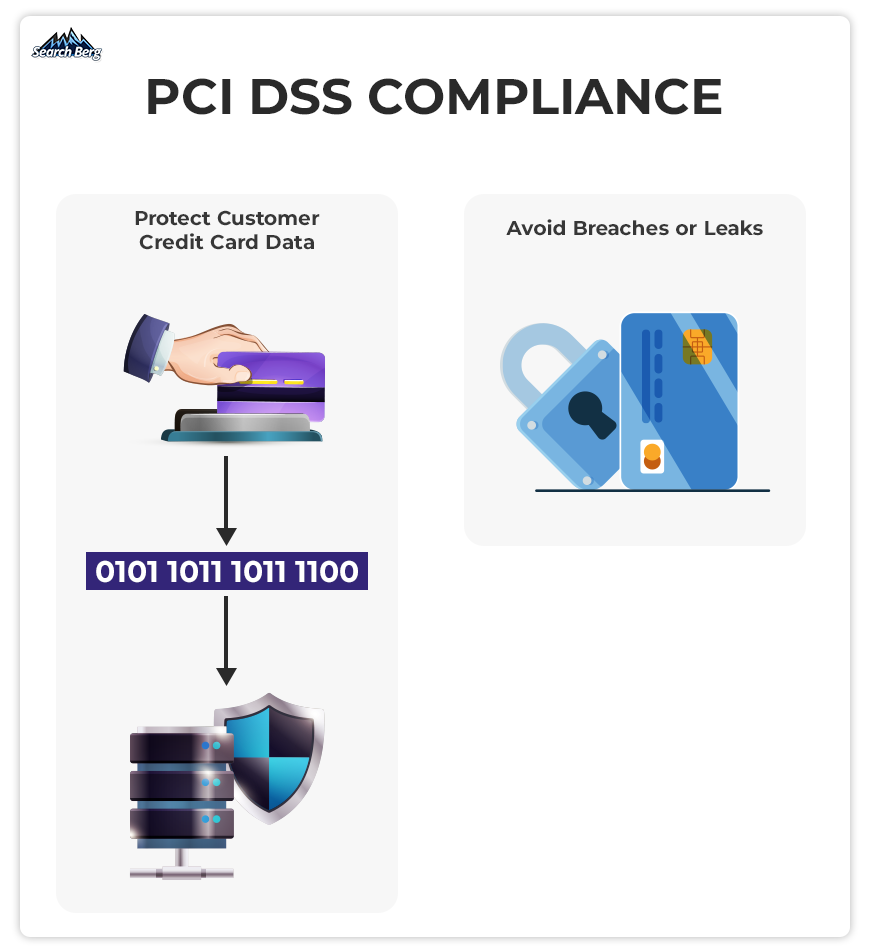
Most secure payment systems follow the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is a comprehensive framework established to guarantee that all businesses handling credit card information uphold a secure environment.
When you’re using a payment gateway that’s PCI DSS compliant, you can rest assured that you’re adhering to the best data security practices.
Let’s consider a hypothetical business, “Hometown Crafts,” as an example. The store is known for selling beautiful handmade décor items online.
Initially, they started with a basic website and an elementary payment process. But as they grew, they realized the importance of secure transactions and switched to a secure, PCI DSS-compliant payment system.
By doing so, they managed to safeguard customer data, prevent potential cyberattacks, and bolster their reputation as a trustworthy online retailer.
A good payment system isn’t just beneficial for secure transactions. It also provides fraud detection features. These features monitor for suspicious activity like multiple transactions occurring in quick succession or transactions of unusually high amounts.
They can identify potential fraud in real-time and prevent transactions from going through before any damage is done.
Secure payment systems often provide tokenization, i.e., the process of replacing sensitive information with unique identification symbols (or “tokens”) that retain all the essential information without compromising its security. This means that even if there’s a breach, the actual sensitive data isn’t stored on your system.
Etsy is an excellent example of a company that takes secure payments seriously. They employ robust security measures, including data encryption and secure socket layer (SSL) technology for data transfer.
Moreover, they’ve established a PCI-DSS-compliant system. Etsy’s secure payment system is one of the many reasons why millions of buyers trust and regularly shop from them.
7. Create Data Backups
Your data is your treasure: a vault of valuable information, including client details, financial records, project blueprints, and more. Imagine if you came in one day to find your vault empty, your treasure gone.
Quite a horrifying scenario, right?
This underscores the importance of backing up your data. To continue with the treasure metaphor, think of data backup as having a reliable, secret map to find your lost treasure or, better yet, a duplicate treasure stowed away safely in another location.
Why is data backup so crucial for your business? For starters, it protects your business from the potentially catastrophic effects of data loss, which could be due to anything from a simple human error, like accidentally deleting an important file, to more disastrous situations like cyber-attacks or natural disasters.
Consider the hypothetical example of a local bakery, “Sam’s Sweets,” that keeps all their customer orders, supplier details, and financial records on a single computer. One unfortunate day, the system crashes, and they lose all their data.
Without a backup, they’d lose orders, miss deliveries, and disappoint their customers. But with a backup system in place, they could quickly restore lost data and continue operations with minimal disruption.
Backing up your data also ensures business continuity. Say, a local marketing firm, “Creative Buzz,” gets hit by a ransomware attack. The cybercriminals lock up their data, demanding a hefty ransom for its release.
But because Creative Buzz regularly backs up its data, they can simply wipe its system clean and restore its files from the backup, bypassing the need to negotiate with cybercriminals.
If you haven’t created a data backup yet, use the right approach to enjoy a secure backup that doesn’t disappoint. We recommend partnering with data protection and privacy experts who can steer you in the right direction.
A robust personal data privacy plan will help you keep your data afloat even when disaster strikes. How can you go about this? Let’s lay out the roadmap.
7.1. External Hard Drives
One of the simplest and most cost-effective methods of backing up data is using an external hard drive. These devices are portable, offer a considerable amount of storage space, and can quickly and easily be connected to your computer or server for data transfer.
The downside is that they can be lost, stolen, or damaged, so they should be stored securely and not be your only backup method.
7.2. Network Attached Storage (NAS) Devices
NAS devices are dedicated devices connected to your network that provide storage accessible to all computers in the network. They’re suitable for small businesses because they offer more storage capacity than traditional external hard drives.
Additionally, multiple users can access and back up their data simultaneously. However, like external hard drives, they can also be vulnerable to physical damage or theft.
7.3. Cloud Backup Services
Services like Google Drive, Dropbox, Microsoft OneDrive, and others provide storage space on their servers, which can be accessed from anywhere with an internet connection. They’re a scalable solution, i.e., you can increase your storage capacity as your business grows.
They also offer high levels of security and automatic backup features. However, they require a reliable internet connection and can come with recurring costs.
7.4. Online Backup Services
These are dedicated backup services like Backblaze or Carbonite that automatically back up your data at regular intervals. They typically offer unlimited or near-unlimited storage for a recurring fee. They’re excellent for “set and forget” backups.
Again, a steady and reliable internet connection is required. Online backup services can also be costly for extensive amounts of data.
7.5. Hybrid Solutions
A hybrid solution involves using a combination of the methods mentioned above. For example, a business could use a NAS device for onsite backups, which offers quick restoration of files, and a cloud or online backup service for offsite backups, providing an extra layer of security in case of physical damage to the onsite backups.
A hybrid approach is generally the smartest call. Consult with cybersecurity and data privacy experts to understand your business’ unique concerns and vulnerabilities. They’ll recommend the most suitable hybrid approach accordingly.
8. Use a Firewall
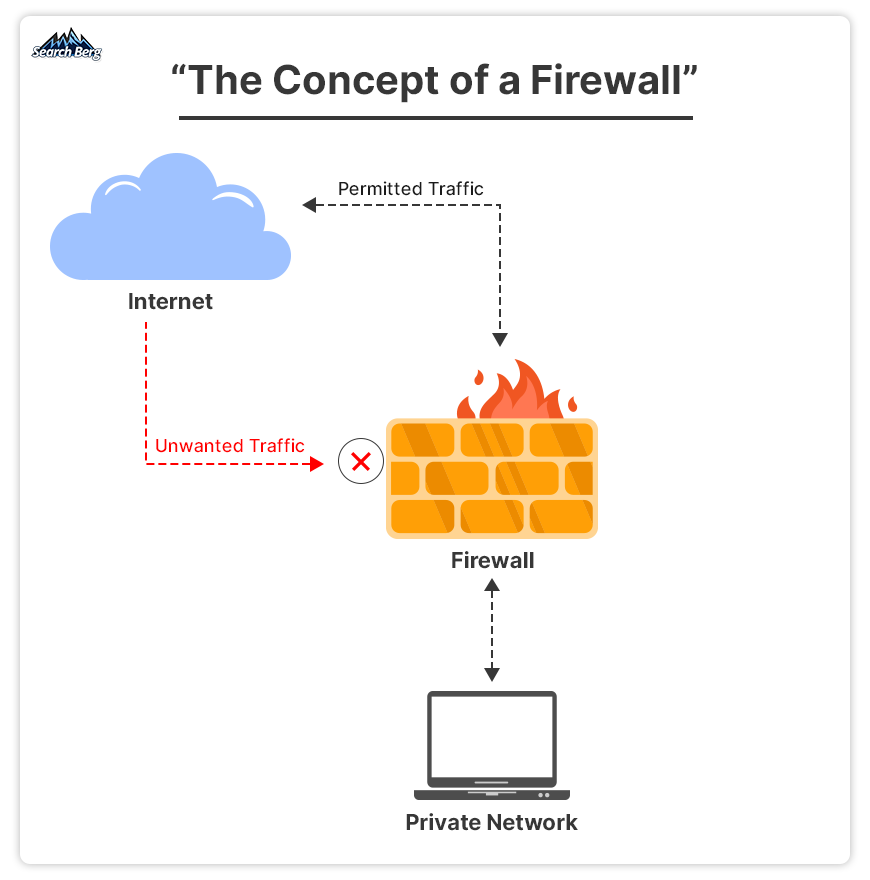
A firewall, in the simplest terms, is a smart security system that carefully monitors and controls the incoming and outgoing network traffic based on a set of fixed security rules.
Just as a physical wall keeps out unwanted visitors, a firewall forms a barrier between your trusted internal network and untrusted external networks like the internet.
When it comes to protecting your privacy online with a robust online privacy protection plan, implementing a firewall is imperative.
There are several types of firewalls available; each offers different functionalities and levels of protection. Let’s explore the most common types of firewalls.
8.1. Packet-Filtering Firewalls
Packet-filtering firewalls represent the fundamental tier of network defense. These firewalls scrutinize individual data packets traversing the network and make decisions based on predefined rules.
These rules encompass filtering criteria like source and destination IP addresses, ports, and protocols. While packet-filtering firewalls possess simplicity and efficiency, they have limited inspection capabilities and may not effectively detect sophisticated attack techniques.
8.2. Stateful Inspection Firewalls
Stateful inspection firewalls go beyond mere packet filtering. They maintain an awareness of the state of network connections, allowing them to analyze entire communication sessions.
By remembering connection states, these firewalls make informed decisions on allowing or blocking traffic. Stateful inspection firewalls provide enhanced security compared to their packet-filtering counterparts and are suitable for most small businesses.
8.3. Proxy Firewalls
Proxy firewalls serve as intermediaries between internal and external networks, acting as gatekeepers for incoming and outgoing traffic.
These firewalls receive requests from internal network users, verify their authenticity, and then forward them to external networks. Similarly, the responses from external networks are validated before reaching internal users.
Proxy firewalls offer added layers of security by concealing internal IP addresses, implementing content filtering, and enforcing application-level security. They’re commonly used to secure web traffic.
8.4. Next-Generation Firewalls
As cyber threats continue to evolve in sophistication, next-generation firewalls (NGFWs) have emerged to address these challenges.
NGFWs combine traditional firewall functionality with advanced features like deep packet inspection, intrusion prevention systems (IPS), virtual private network (VPN) support, and application awareness.
This multifaceted approach empowers NGFWs to identify and thwart a wide range of threats, including malware, malicious code, and unauthorized access attempts.
Moreover, NGFWs provide granular control over network traffic, allowing administrators to define policies based on application, user, and content.

8.5. Unified Threat Management (UTM) Firewalls
Small businesses with limited IT resources benefit from the holistic security approach offered by UTM firewalls. These firewalls integrate multiple security features into a single appliance.
UTM firewalls combine traditional firewall functionality with antivirus, anti-spam, web filtering, and intrusion detection and prevention systems. This consolidated approach streamlines network security management while providing robust protection against various threats.
Start Protecting Your Business with Search Berg
The digital era has brought a multitude of opportunities for small businesses. However, each shiny opportunity comes with an ominous challenge.
If you hastily and recklessly aim for shiny new opportunities without keeping the threatening landscape in mind, you’ll set yourself up for failure.
That’s what we’re here for. At Search Berg, we want to help you reap all the benefits digital marketing has to offer. At the same time, we want you to tread carefully and protect your business.
If you haven’t turned your attention to online privacy protection for small business owners yet, it’s time. Our experts are ready to show you the way! Once we’ve steered you in the right cybersecurity and data privacy direction, we’ll take the digital marketing reins and let the real fun begin.
Security and safety? Check.
An envious online presence, high SERP rankings, impressive traffic, and roaring sales? We got it!
Explore our SEO services and affordable SEO packages to get started! In addition to taking the SEO reins, we also keep an eye on our clients’ cybersecurity measures. If we feel that your website isn’t secure, we’ll alert you and provide a rough roadmap.
It’s all systems go!